blog.trailofbits.com/2025/04/21/jumping-the-line-how-mcp-servers-can-attack-you-before-you-ever-use-them
Preview meta tags from the blog.trailofbits.com website.
Linked Hostnames
9- 10 links toblog.trailofbits.com
- 2 links togithub.com
- 1 link togohugo.io
- 1 link toinfosec.exchange
- 1 link toinvariantlabs.ai
- 1 link tolinkedin.com
- 1 link tomodelcontextprotocol.io
- 1 link tonews.ycombinator.com
Thumbnail
Search Engine Appearance
Jumping the line: How MCP servers can attack you before you ever use them
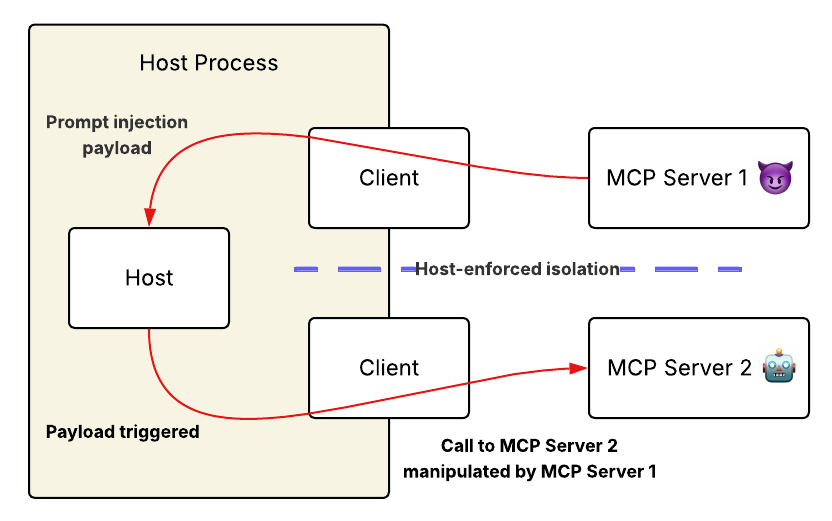
This post is about a vulnerability in the Model Context Protocol (MCP) called “Line Jumping,” where malicious servers can inject prompts through tool descriptions to manipulate AI model behavior without being explicitly invoked, effectively bypassing security measures designed to protect users.
Bing
Jumping the line: How MCP servers can attack you before you ever use them
This post is about a vulnerability in the Model Context Protocol (MCP) called “Line Jumping,” where malicious servers can inject prompts through tool descriptions to manipulate AI model behavior without being explicitly invoked, effectively bypassing security measures designed to protect users.
DuckDuckGo
Jumping the line: How MCP servers can attack you before you ever use them
This post is about a vulnerability in the Model Context Protocol (MCP) called “Line Jumping,” where malicious servers can inject prompts through tool descriptions to manipulate AI model behavior without being explicitly invoked, effectively bypassing security measures designed to protect users.
General Meta Tags
7- titleJumping the line: How MCP servers can attack you before you ever use them - The Trail of Bits Blog
- charsetUTF-8
- viewportwidth=device-width,initial-scale=1
- description
- article:sectionposts
Open Graph Meta Tags
7- og:urlhttps://blog.trailofbits.com/2025/04/21/jumping-the-line-how-mcp-servers-can-attack-you-before-you-ever-use-them/
- og:site_nameThe Trail of Bits Blog
- og:titleJumping the line: How MCP servers can attack you before you ever use them
- og:descriptionThis post is about a vulnerability in the Model Context Protocol (MCP) called “Line Jumping,” where malicious servers can inject prompts through tool descriptions to manipulate AI model behavior without being explicitly invoked, effectively bypassing security measures designed to protect users.
og:locale
en_us
Twitter Meta Tags
4- twitter:cardsummary_large_image
- twitter:imagehttps://blog.trailofbits.com/img/mcp-series/prompt-injection-tool.png
- twitter:titleJumping the line: How MCP servers can attack you before you ever use them
- twitter:descriptionThis post is about a vulnerability in the Model Context Protocol (MCP) called “Line Jumping,” where malicious servers can inject prompts through tool descriptions to manipulate AI model behavior without being explicitly invoked, effectively bypassing security measures designed to protect users.
Link Tags
11- dns-prefetch//fonts.googleapis.com
- dns-prefetch//fonts.gstatic.com
- preconnecthttps://fonts.gstatic.com
- preload stylesheet/css/syntax.css
- shortcut icon/favicon.png
Links
19- https://blog.trailofbits.com
- https://blog.trailofbits.com/2025/04/29/deceiving-users-with-ansi-terminal-codes-in-mcp
- https://blog.trailofbits.com/2025/04/30/insecure-credential-storage-plagues-mcp
- https://blog.trailofbits.com/2025/05/01/making-pypis-test-suite-81-faster
- https://blog.trailofbits.com/2025/05/02/datasig-fingerprinting-ai/ml-datasets-to-stop-data-borne-attacks